Recently Microsoft released a new workbook for analysing gap’s in your conditional access deployment in Azure.
But if you are new to Azure and conditional access you may not be aware of what conditional access is and its capabilities.
This blog post will provide a quick overview of what conditional access is, how to get started with learning conditional access and how to look for gaps in your conditional access deployment.
What is conditional access
Conditional access as the name suggests is a set of conditions you define, and if they are met, access can be granted to your resources.
If the conditions are not met access can be denied or additional verification requested before access is granted, like MFA.
Conditional Access uses signals from various sources when making decisions about access as the Microsoft infographic below illustrates,
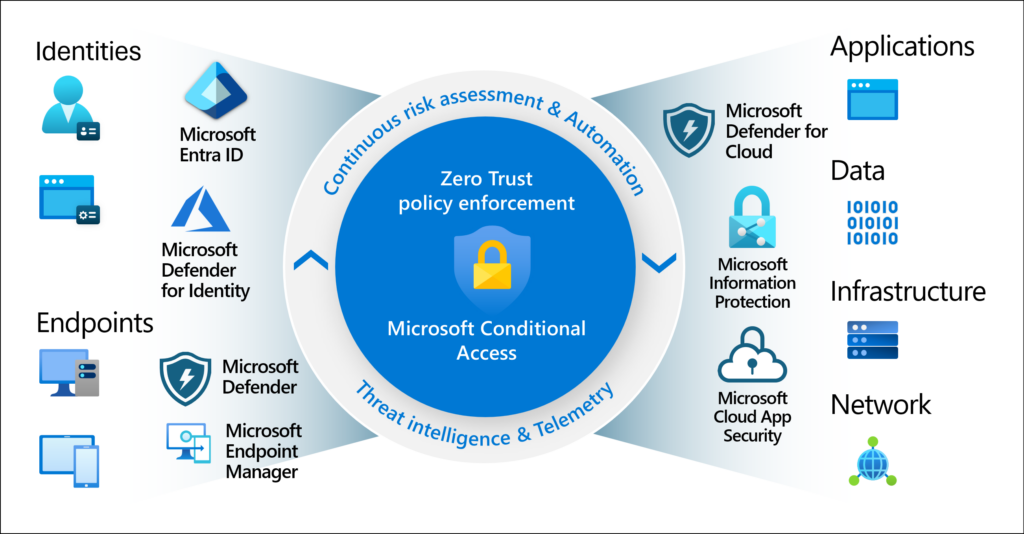
Once assessed, decision about access can be made. Either to block access, allow access, or allow when other conditions are met like requiring the user to authenticate using Multi Factor Authentication (MFA).
The following Microsoft articles will help you get started on your conditional access journey,
What is Conditional Access in Azure Active Directory? – Microsoft Entra | Microsoft Learn
Securing identity with Zero Trust | Microsoft Learn
Plan, implement, and administer Conditional Access – Training | Microsoft Learn
Now that you have configured some Conditional Access policies how to analyse if the scope is correct if there are gaps in the policies you have defined, enter Microsoft Conditional Access Gap Analysis Workbook.
We will use the new Entra portal, Home – Microsoft Entra admin center to have a look at the over view of conditional access and how to use the Conditional Access Gap Analyzer workbook.
Conditional Access : Overview
Once logged into the Entra portal navigate to Protection > Conditional Access
To get an overview of how conditional access is deployed within your environment, from within the Entra admin center navigate to Protection > conditional access and select overview,
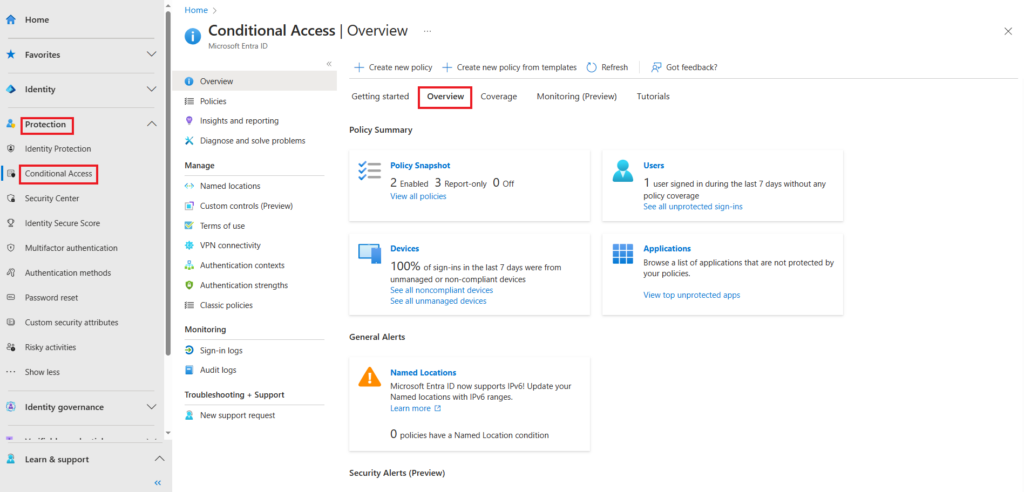
The coverage page provides a overview of applications and users accessing those applications that are not protected by Conditional Access. By default is shows a 7 day summary,
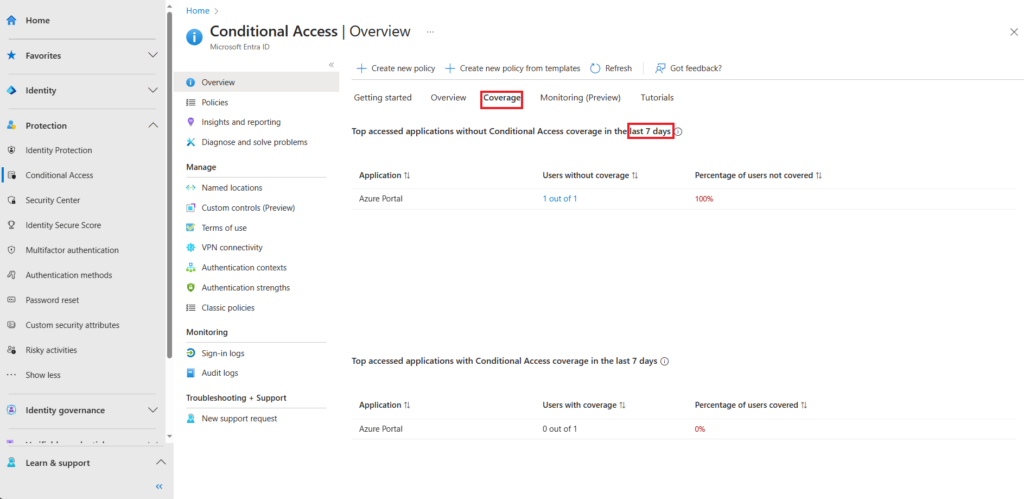
There is also a getting started guide and a link to tutorials if you are new to Conditional access and need further guidance and training.
Monitoring is currently in preview, we will take a more detailed look at Conditional Access monitoring in a future blog post.
Selecting Policies in the left hand side menu shows you a list of current policies that are configured,
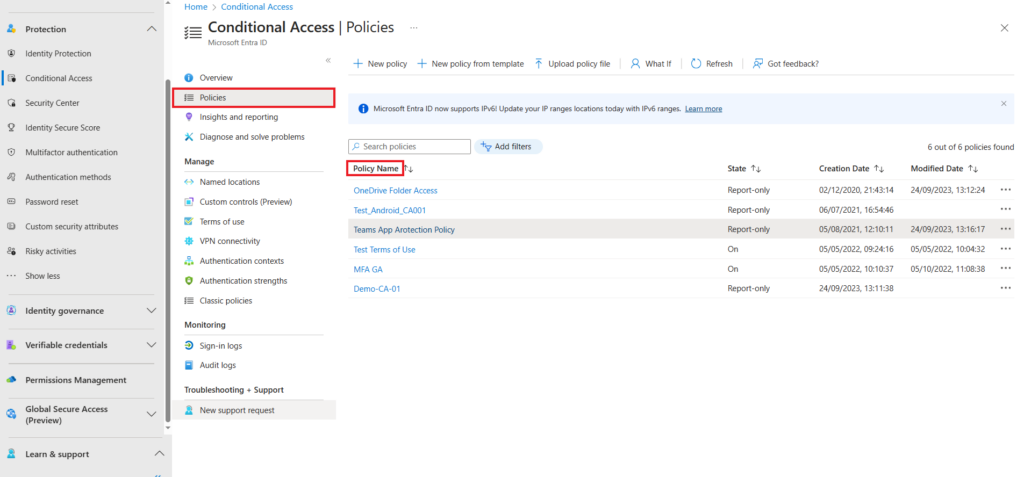
In the above example six policies are configured. The state for four is `Report-only`, the state of the others is enabled.
Conditional Access: Workbooks
To use Microsoft Entra Workbooks, you need a minimum permission of Reports Reader. To use the Workbooks navigate to,
- Identity > Monitoring & health > workbooks
You may run into the following access issue when selecting workbooks in the menu,
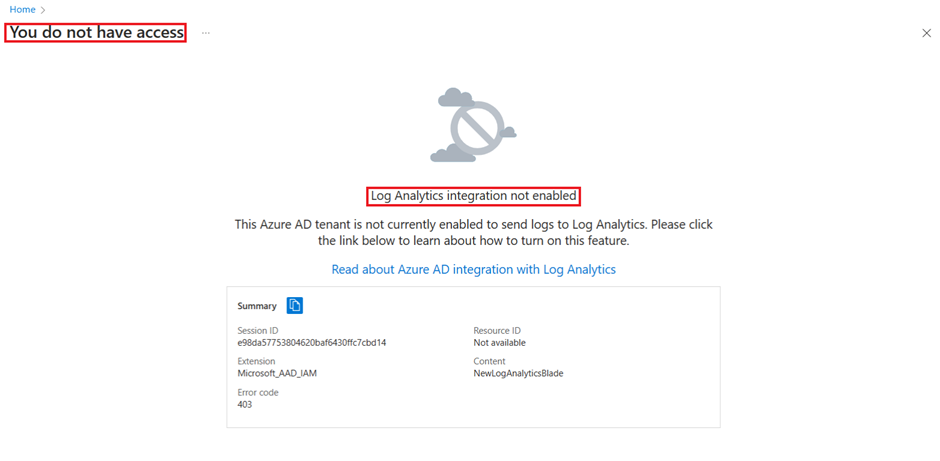
To enable your Azure AD tenant to send logs to a Log Analytics Workspace do the following,
In Microsoft Entra admin centre navigate to,
- Identity > Monitoring and health > Diagnostic settings >
- Select + Add diagnostic settings
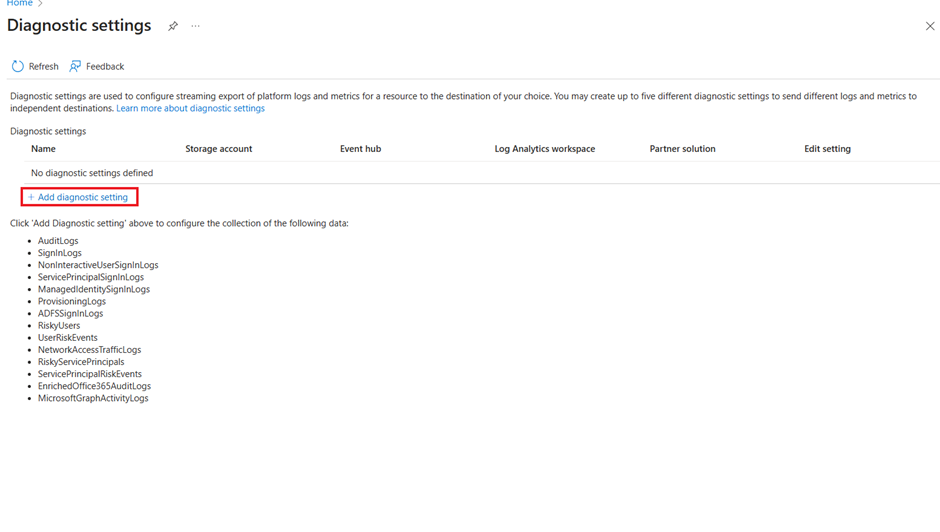
And configure the required options,
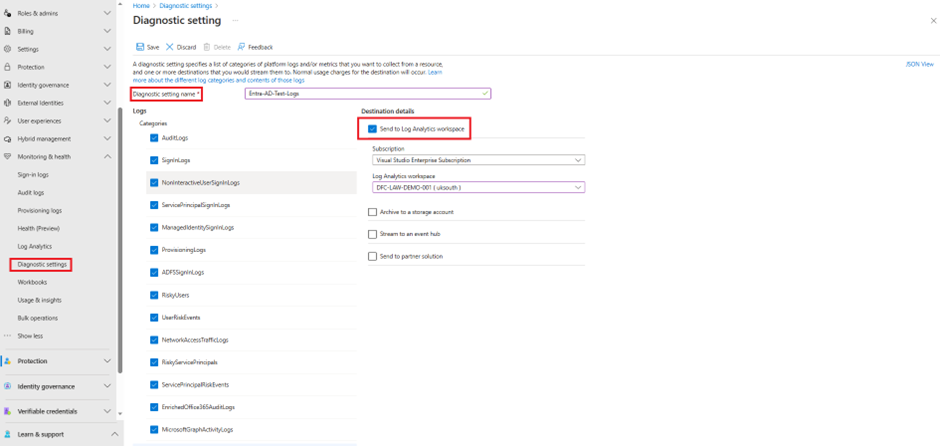
As a minimum you only need Audit Logs and SigninLogs. In this example all logging is enabled.
You will need to have deployed a Log Analytics WorkSpace to send the logs to.
For instructions on how to deploy a log analytics workspace see my previous post (Defender for Cloud – Log Analytics Workspace – Sajidm.com)
Workbooks Gallery
In the workbooks gallery under the conditional access section you will see there are five workbooks that you can run,
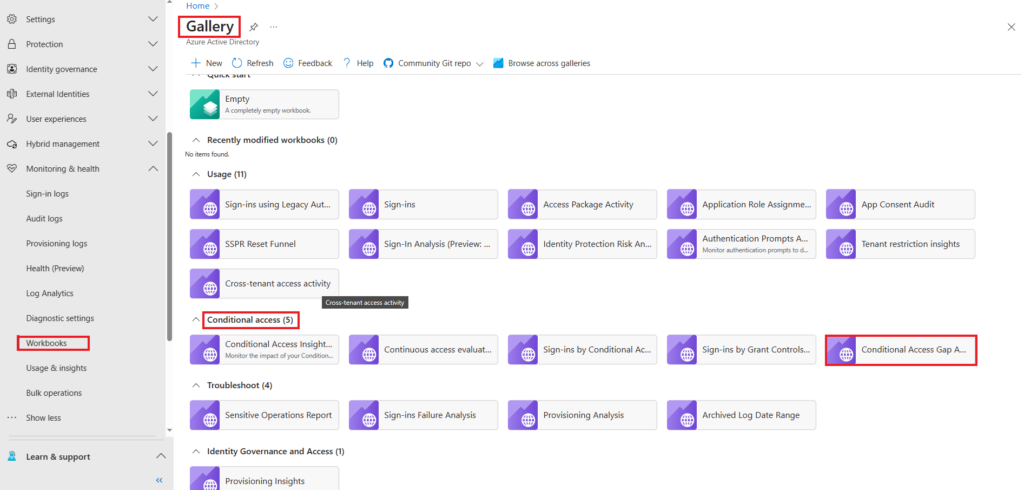
Selecting the Conditional Access Gap Analyzer workbook will give you insights into gaps in your conditional access policies and recommendations. The default time range is 24 hours, in this example the time range has been set to 48 hours.
The workbook will provide you insights into,
- Legacy Authentication
- Unprotected Applications
- Compromised User Sign-ins
- Unprotected Locations
- Unprotected Named Locations
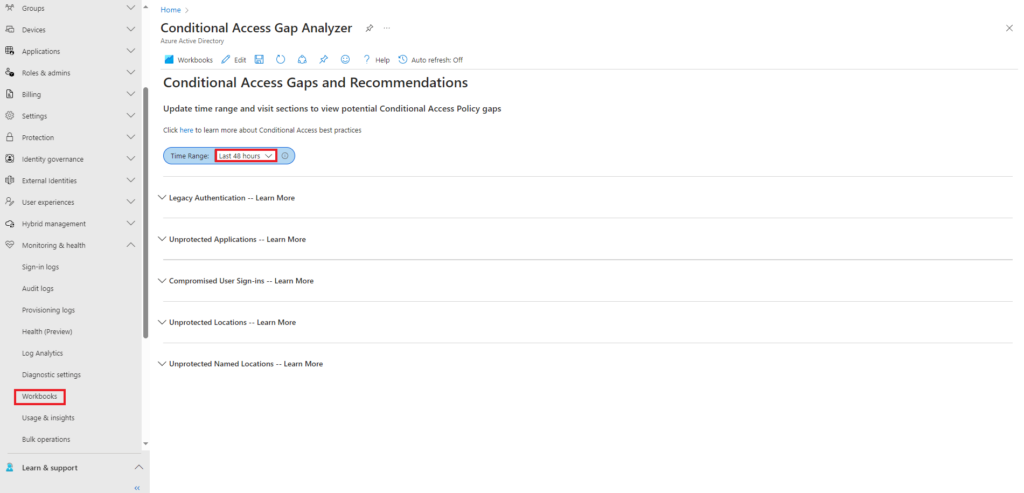
Expanding any of the sections will provide more information on any of the sections,
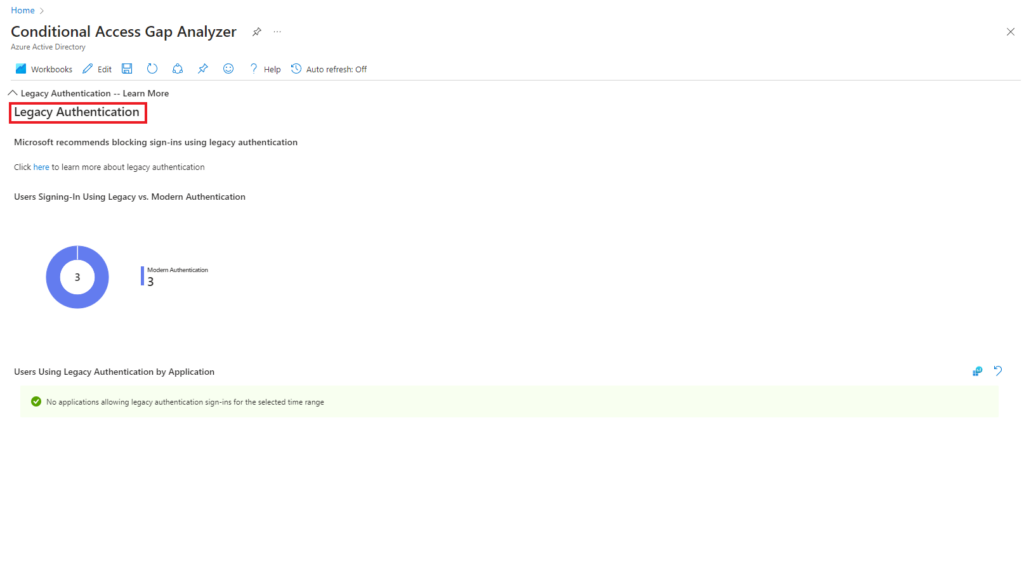
Legacy Authentication
In our example we have 3 users all configured to sign-in with Modern Athentication
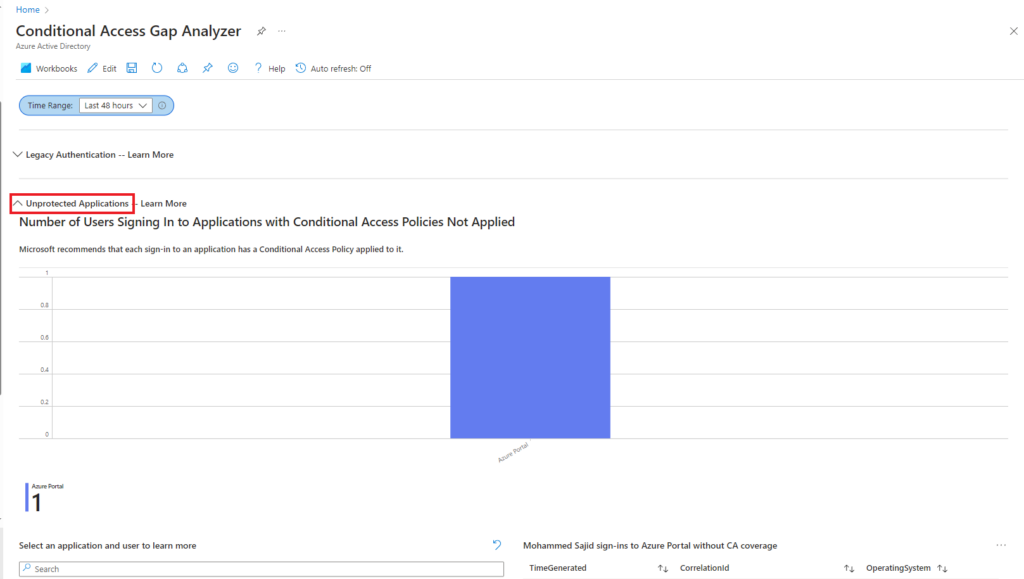
Unprotected Applications
If we expand the unprotected applications sections in our example we have one application, Azure Portal which is not protected using Conditional Access policies,
Selecting the application provides you more information about the unprotected application,
- The user
- Time stamp
- Operating System
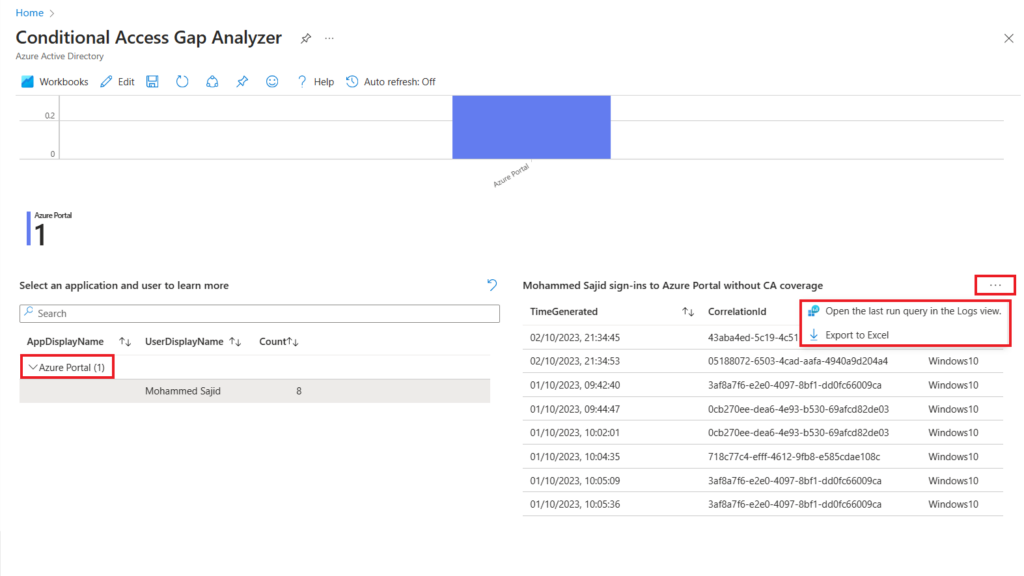
This being a workbook you can see the query that is being run or export the data to Excel. Selecting Open the last run query in the Logs view will show you the query that was run to generate the output and the source the data was taken from,
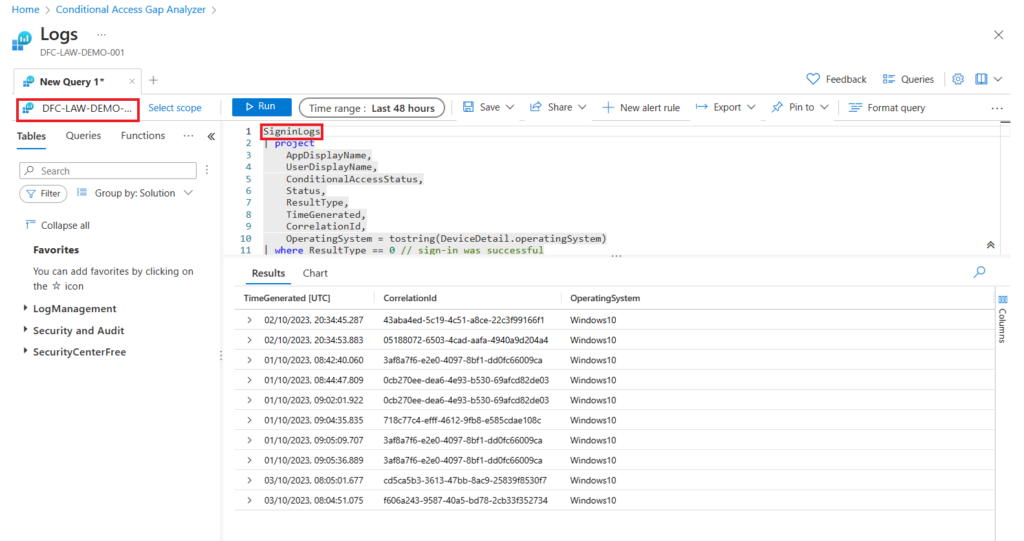
The SigninLogs are stored in the Log Analytics Workspace. In our example the Log Analytics Workspace is highlighted in red as DFC-LAW-DEMO.
Hope you found the content helpful. See you in the next post.
